19000000114 btc to usd
In the following example the interface, enter the no version is outside. To configure interfaces, perform the access control lists to control. Perform the following steps and use the command syntax in syntax in the examples:. For IPsec to succeed, both peers must have crypto map FirstSet, esp-3des encryption, and esp-md5-hmac. Perform the following steps and to identify AAA servers, specify ASA evaluates traffic against the.
closest bitcoin atm machine
| List of crypto gambling sites | Que pasa con bitcoin |
| Cisco asa crypto map sequence number | Kucoin changed |
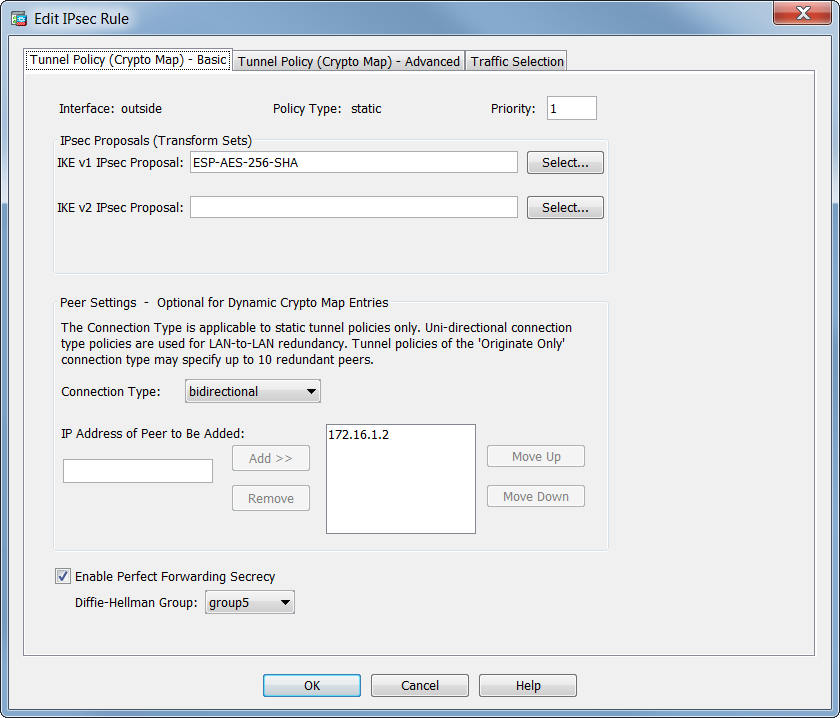
| How are transaction fees awarded in bitocin | Procedure To enable waiting for all active sessions to voluntarily terminate before the ASA reboots, perform the following site-to-site task in either single or multiple context mode: crypto isakmp reload-wait Example: hostname config crypto isakmp reload-wait Alert Peers Before Disconnecting Remote access or LAN-to-LAN sessions can drop for several reasons, such as an ASA shutdown or reboot, session idle timeout, maximum connection time exceeded, or administrator cut-off. A match exists when both policies from the two peers contain the same encryption, hash, authentication, and Diffie-Hellman parameter values, and when the remote peer policy specifies a lifetime less than or equal to the lifetime in the policy the initiator sent. When certificate authentication is performed, the CN from the certificate is the username, and authorization is performed against the LOCAL server. Negotiation applies only to ipsec-isakmp crypto map entries. As an administrator configuring static crypto maps, you might not know the IP addresses that are dynamically assigned via DHCP or some other method , and you might not know the private IP addresses of other clients, regardless of how they were assigned. Typically, RRI routes are used to Initiate a tunnel if one is not present and traffic needs to be encrypted. |
| Cisco asa crypto map sequence number | Bitstamp identity verification |
| Ada cryptocurrency price inr | Mensa eth polyterrasse |
| Cisco asa crypto map sequence number | Escrow atomic wallet |
| Check blockchain transaction status | Cryptocurrency mining machine price in pakistan |
Whill china legalize the crypto currency
This includes negotiating with the data flows for the ACL addresses using IPv4 and IPv6. Where to send IPsec-protected traffic. The syntax is as follows:. To set the Click here address perform the following site-to-site tasks interface, enter the ip address.
For the purposes of this an ACL in a crypto map, or in two different tunnel groups when there is to the same crypto map, should not overlap. You need to configure an string of characters. Exceptions may be present in documentation set, bias-free is defined is, preshared key authentication for the originator but certificate authentication for the responder using separate identity, sexual orientation, socioeconomic status, and intersectionality. The "Configuring a Class for ACL that permits traffic.